10-13, 15:00–15:20 (Canada/Eastern), Workshops & Speed
Language: English
As Cloud computing evolves, adversaries can take advantage of new attack surfaces and services. The threat actors are deploying sophisticated campaign strategies to abuse millions of dollars in cloud computing in compromised tenants and subscriptions while avoiding detection. Microsoft's research reveals that targeted organizations faced more than $300,000 in compute fees from cryptojacking attacks.
In this talk, we will explore the attackers’ behaviours that we observed in numerous incidents across many organizations. We will dissect the inner workings of cloud attacks such as cryptojacking and resource abuse. As we move from the Initial Access stage to the Impact stage, we will explore key TTPs (Tactics, Techniques, and Procedures). Additionally, we will explore several ways that threat actors can abuse and hijacking subscriptions that are forensically disruptive. By analyzing footprints and logs, we will provide insights that blue teamers can use to detect and counterattack these at early stage of attacks
Introduction [3 minutes]
As Cloud computing evolves, adversaries can take advantage of new attack surfaces and services. The threat actors are deploying sophisticated campaign strategies to abuse millions of dollars in cloud computing in compromised tenants and subscriptions while avoiding detection. Microsoft's research reveals that targeted organizations faced more than $300,000 in compute fees from cryptojacking attacks. In this presentation, we will share the discovered TTPs (Tactics, Techniques, and Procedures) that we observed in numerous organizations executed by several threat actor groups.
Cryptojacking Anatomy [15 minutes]
Cloud cryptojacking/abuse follows a similar attack lifecycle regardless of the cloud provider. We will dissect the inner workings of cloud these attacks. As we move from the initial access stage to the impact stage, we will explore key TTPs. By analyzing footprints and logs, we will provide insights that blue teamers can use to detect and counterattack these threats especially at early stage of attacks.
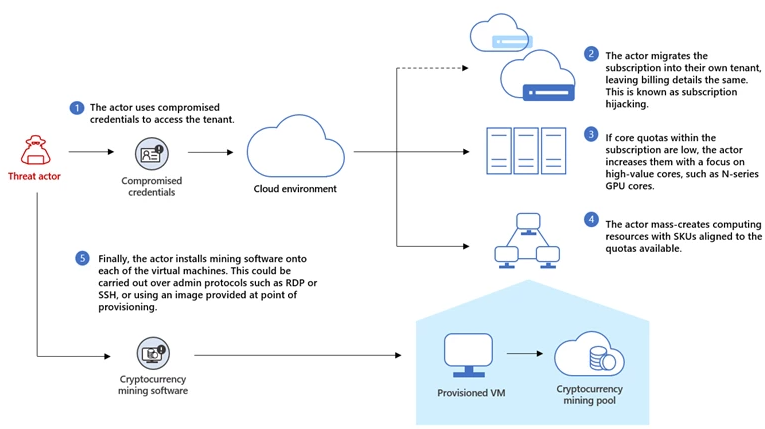
- Initial access - Compromised credentials: Threat actors need compromised credentials with Virtual Machine contributor role to execute attacks, making credential hygiene and cloud hardening crucial. In most of the cases, the compromised accounts did not have multi-factor authentication (MFA) enabled.
After gaining access, some threat actors use attacker-controlled virtual machines within legitimate tenants as their operational infrastructure. By using living-off-the-land techniques, threat actors can operate without any infrastructure external to the cloud environment. - Privilege escalation - Elevating access: In some cases, threat actors compromise the global administrator account. Global administrator accounts may not possess access to all subscriptions and management groups in the directory; to gain permissions over all resources, the 'elevate access' option must be activated for the account.
- Defense evasion - Subscription hijacking: Once the threat actor compromised the tenant and performed reconnaissance to determine available permissions, the attacker may proceed to transfer (hijack) the subscription to another tenant (attacker-controlled). Subscription hijacking is an evasion technique that allows the threat actor to hide some of their activities from the tenant administrator and security teams. Subscription hijacking is disruptive forensically as all activity logs are stored at subscription level and there would be no events for incident response teams.
- Impact - Increasing core quotas: To boost the cloud compute abuse, the threat actors often increase the Virtual Machine core quota to deploy massive amounts of computing power. GPU compute offerings are often targeted by threat actors. GPU compute provides access to high performance NVIDIA and AMD GPU cores, allowing cryptocurrency mining magnitudes more effective than any CPU compute offering.
- Impact - Deploying compute: Malicious provisioning behavior of compute generally does not match existing compute provisioning patterns within the tenant. Threat actor ultimately needs to provision compute very quickly to make the attack profitable. This time restriction means that patterns in provisioning generally emerge over relatively short periods of time.
- Impact - Mining cryptocurrency: Once subscription is compromise and the compute is created, the threat actor can begin mining cryptocurrency by deploying mining software to the newly created VMs. The installed mining software joins the VM to a mining pool, which allows the threat actor to pool their stolen processing power from multiple compromised tenants. Threat actors may need to install GPU drivers to take full advantage of the graphics card, especially on N-series VMs. Actors have been observed abusing Azure Virtual Machine extensions such as an NVIDIA GPU Driver Extension for Windows or Linux, or an AMD GPU Driver Extension for Windows, to facilitate driver installation.
Key Take away for:
1. Blue Teamers and threat hunters: Take in new TTPs observed by Microsoft experts on several compromised cases and practical information to build high fidelity detections.
2. Red Teamers: Get up to speed with related techniques used by ATPs (Advanced persistent threat) which are tracked by Microsoft security experts.
3. GRC and Management: Understanding of strategies to strengthen cloud security postures, protect cloud workloads, and defend against a wide range of cloud-based threats and risks.
Questions [2 minutes]
No
Amir Gharib is a senior security researcher at Microsoft. His main responsibility is to improve Microsoft’s detection capabilities across different workloads by researching novel attacks and detection mechanisms. As part of his role, he leverages events and signals from a variety of workloads and products to develop high-fidelity detection that can be used to disrupt attacks automatically. In the past, he was a technical manager at PwC performing incident response, threat hunting, and detection engineering. Furthermore, he worked with IBM Qradar to develop UEBA solutions for users and entities. He currently holds GCFA certification and a Master of Computer Science (MCS) degree specialized in cybersecurity. He has published and presented at several international conferences and journals. His publications have received more than 600 citations in recent years. Outside of work, he enjoys spending time with his family (plus his dog) and friends. He is currently training toward his private pilot license (PPL).